News
What Is a DDoS Attack? (Hint: It Involves Zombies & Traffic Jams)

A distributed denial of service (DDoS) attack is kind of like a traffic jam on a website What is a DDoS attack and what does it mean for your website? Instead of jumping deep into technical details, let’s start with a real-world analogy that makes it really easy to visualize what a DDoS attack is… Imagine, for a moment, that it’s a Sunday afternoon and you’re driving down the highway with your family, headed to your favorite picnic spot. You’re cruising down the highway at 70 miles an hour – it won’t be long before you’re at the park enjoying a lovely autumn day! …That is, until you go around a curve and see this in front of you:

It’s a traffic jam — going as far as the eye can see! You check your GPS traffic report, only to see that the jam extends for miles and there’s no way around it. There’s no way you’ll make it to the park in time for your picnic.
That’s basically how DDoS attacks work – lots of users (in this case, cars) that are jamming up a system (the highway) to deny you from accessing a service (the park).
Usually when we talk about DDoS attacks, the resource being denied is a website and the “traffic jam” was maliciously caused by a hacker. But the concept is the same as a traffic jam on the highway. Let’s dive into what DDoS means, the types of DDoS attacks, and methods of DDoS prevention.
Let’s hash it out.
What is a DDoS Attack? A Simple Definition
Since we’re all about making technical topics simple, let’s start with a basic answer to the question: What does DDoS mean (a.k.a. “What is a distributed denial of service attack”)? As mentioned above, a DDoS attack is a bit like a traffic jam on a website (but it’s intentionally caused by a hacker).
Here’s a simple definition for the meaning of DDoS:
“A DDoS (distributed-denial-of-service) attack is when a hacker makes a website or other service inaccessible by flooding it with requests from many different devices.”
If you’ve also heard the term “DoS attack,” don’t let that confuse you. A DDoS attack is just a specific type of DoS (denial-of-service) attack — one that uses multiple computers/devices to attack with.
How Does a DDoS Attack Work? (Hint: It Involves Zombies!)
Just like a traffic jam floods a highway with more cars than it can handle, a DDoS attack floods a website with more requests (i.e. visitors) than the web server or other related systems can handle.
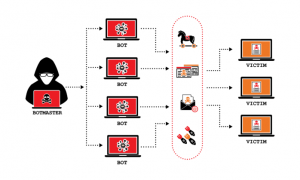
Many hackers use botnets (a.k.a. zombie computers) to execute DDoS attacks. A botnet is a way for a single person (hacker) to control thousands of devices at once.
Here’s how a botnet works to execute a DDoS attack:
Step 1: Building the Botnet
To create a botnet, a hacker needs a way to take control of thousands of devices — these could be computers, mobile phones, or IoT devices such as webcams or smart refrigerators. There are quite a few ways the hacker could find and take control of these devices. For example, they might write a virus that propagates and gradually takes over more and more computers. Or, they might find a specific IoT device with a known vulnerability (for example, poor default login security) and build a bot to scan the internet and hack as many of those devices as possible. If you want to read more about how hackers do this, check out our post on Hacking IoT Devices: How to Create a Botnet of Refrigerators.
Step 2: Controlling the Botnet
As the hacker takes control of each device, they’ll do something so it will obey any instructions the hacker sends to the device. (For example, installing a small program on it.) There are a few different approaches the hacker can use (client-server model, P2P model based on digital certificates, etc.), but the end result is the same — the hacker can issue a command and all the devices in the botnet will do whatever the hacker instructed them to do.
Step 3: Executing the Attack
Once the hacker has thousands of devices at his beck and call, he can execute the DDoS attack. There are a few different types of DDoS attacks (more on that later), but the basic idea is the same: flood a web server with more requests than it can handle. The attacker will typically research the target website carefully to identify a weakness to exploit, then craft a request that will target that vulnerability. Finally, the attacker will instruct their zombie computers to execute that request (repeatedly). Here’s an example: Let’s say Bob’s botnet has 100,000 devices in it. He issues a command to the botnet to send an HTTP request to example.com once per second. That’s 60 visits per minute times 100,000 devices. That adds up to 360 million visits per hour, or 8.6 billion visits per day. That’s far more than most web servers are designed to handle. If the attack was planned well, the web server will be overloaded and any real people who try to visit the site will get an error message. DDoS attack success!
DDoS the Lazy Way: Rent a Botnet!
If it sounds like a lot of work to build a botnet and execute a DDoS attack, you’d be right. But (unfortunately) there’s an easier way — lazy attackers can just go on the dark web and rent a botnet for as little as $10 per hour! Cybercrime is a booming industry, and services such as DDoS botnet rentals and phishing as a service solutions are just a few of the options available for purchase.
Types of DDoS Attacks
Our simplified definition of what DDoS is left out one detail: there are many different types of DDoS attacks that attackers can use depending on what specific server resource they’re trying to overload. Since we’re trying to keep things simple, we’ll just briefly highlight the broad types of DDoS attacks commonly used. As mentioned previously, DDoS attacks are designed to jam up a website, usually by overloading a specific aspect of the site. For example, an attack could target the following to overload them: Web server resources such as CPU or RAM Database servers Network bandwidth DNS servers Etc. As Gregory Kelley, Chief Technology Officer at Vestige Digital Investigations, explains:
“DDoS attacks can be categorized as either volume based or application based. Volume based attacks will attempt to flood a website, server or internet connection with more traffic than it can handle. Application based attacks usually look to exploit a vulnerability or defect in a protocol to tie up a specific service, such as a website.”
The Motive Behind the Attack: Why Do Hackers DDoS?
“Some men aren’t looking for anything logical, like money. They can’t be bought, bullied, reasoned, or negotiated with. Some men just want to watch the world burn.” Alfred Pennyworth, The Dark Knight
Sometimes, DDoS attacks have a direct goal in mind (such as money). In other cases, people just want to cause trouble and feel powerful. Gregory Kelley explains that the top reasons he sees are: Financial gain. The hacker may be seeking to hold a company at ransom – demanding that they pay money to stop the attack. Diversion. Another reason is to distract a company’s cyber defenses so that the hacker can try to infiltrate the company in another fashion. Hacktivism. The hacker could be doing it to protest actions on the part of a company or government (such as the case of James Robinson).
Are DDoS Attacks Illegal?
Short answer: yes.
Slightly longer answer: The specific laws around DDoS vary depending on where you’re located. Some countries have lax laws (or insufficient enforcement), so DDoS attackers may operate out of those countries.
In the U.S., DDoS attacks are illegal under the Federal Computer Fraud and Abuse Act. The punishment can be substantial, too — up to 10 years of prison and up to $500,000 in fines. In fact, a man from Connecticut recently got a 10-year prison sentence for DDoS attacks against hospitals.
Identifying and prosecuting attackers is often complex, since the attacks commonly span multiple countries. As Maria Sirbu from Voxility explains:
“DDoS attacks often involve tools from several countries: the target IP is located in one country, the attacker is located in another, the command and control servers are in a different country, and the bots used in DDoS attacks come from multiple places. For this reason, investigating attacks, blocking botnets and discovering attackers has become serious business.”
DDoS Mitigation: What You Can Do If You’re Attacked
As DDoS attacks are becoming bigger and more common, the tools we have to fight back have gotten better, too. Now even the smallest businesses can get good DDoS prevention solutions. (Although most DDoS attacks still target larger companies.) Here are a few tactics any website owner can implement to protect their site: Contact your web host to find out what their policies and protections are against DDoS. Contact your DNS provider to see if they protect against DNS flood attacks. Use a content delivery network (CDN) with a web application firewall (WAF) and DDoS protection built in. Essentially, the CDN sits between the attacker and your web server, so it can dilute and/or block the attack before it reaches your web server.
ONLINE ARTICLE FROM:
 by Adam Thompson
by Adam Thompson
hashedout by the SSL Store
Read more at: https://www.thesslstore.com/blog/what-is-a-ddos-attack/”