Articles
Assuring Your Text Messaging Evidence Is Not Spoofed

Americans send millions of text messages each day. Frequently, those text messages can contain information which becomes relevant to a lawsuit or investigation. The influential effect of those spoofed text messages upon the matter completely depends on their validity. Prior to their use as evidence, text messages should be validated to ensure that the text message was actually sent and not just created to influence or justify an investigation or litigation. Continue reading this post to learn more about authenticating text messages for evidence in an investigation.
Casework Example
In early 2019, Vestige was contracted to review the evidence for a matter in New York City where our client was alleged to have sent defamatory text messages. The messages were sent in 2016 and there was only a limited amount of digital forensic evidence available for us to review. However, we were able to examine screenshots of the text messages along with the carrier bills and cell tower records.
Our first challenge was to determine the possible ways the text messages could appear on the recipient’s phone without evidence of their originating from our client. There are many ways to create text messages that appear to be authentic by duplicating the structure and appearance of actual messages from common text applications. Many applications can be located on the Apple App store, Google Play Store, or on the internet to create text messages with content that will appear authentic. Identifying information of the sender such as phone number or contact name can appear in the sender field. Any characters, photos or .gifs can be placed in the spoofed message that can be found in a real message. Many apps allow customization of the display of the message to conform with carrier, phone type, and operating system running on the phone.
Validation is Key
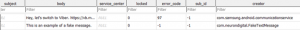
Before the content of a text message can be substantiated, the message should be validated using accepted forensic tools and methods by an accredited forensic expert. A forensic image of the device and review of the text message database will show the source of the message. As shown in the excerpt from the mmssms.db table below from an Android OS phone, the spoofed text message is shown as being sent by com.neurondigital.FakeTextMessage.
Display of a text message on the screen of the phone is not sufficient to prove that the message is authentic. Many applications exist that convincingly create text messages and allow the creator to attribute the message to a random or specific name or contact. Without a forensic image, it may be difficult to defend against accusations with a convincing appearing message. For more information on how forensic experts spot fake screenshots and fake text messages, please see Vestige Blog by Ian Finch.
Another key source of supporting data for a text message evidence investigation is the carrier invoice. Depending on the communication carrier, information for each call and text message such as the date, time, phone numbers (sending and receiving) along with location may be included. Be sure to make a timely request for this data from the carrier to be sure to get the most complete information possible. Remember that the carrier will not have a record of messages sent via 3rd party application or via the Internet such as iMessages sent from iPhone to iPhone.
Utilize a Forensic Expert
Vestige is an excellent resource to keep in your hip pocket, in regard to Digital Forensics, Cybersecurity – particularly Reactive Data Breach and Incident Response matters, in addition to Proactive services. We are accustomed to being parachuted in and are known for our speed and accuracy. Our standard turnaround is within two weeks, with capability of 72-hour turnaround for emergency matters. As Digital Evidence Experts we serve as neutral experts in courts of law. We are established and well-respected in the legal community.
Should you have ANY questions regarding digital devices, data breach/incident response and preserving and/or validating valuable data and evidence – Contact Vestige today, we are happy to help.